Research: More than 56% of all cryptocurrency crime happens in the US
The rate of cryptocurrency hacks is rapidly increasing. 720 accounts across every major exchange have been compromised — and a lot of it has to do with poor security setups, especially the lack of two-factor authentication (2FA).

International cybersecurity firm Group-IB has shown that the number of compromised accounts has risen 369 percent since 2017. Data shared with Hard Fork shows that a staggering third of all victims were located in the US. E very single one of the top 19 exchanges has been hit; 720 usernames and passwords stolen in total.
The rate of hacks even mirrored market highs when incidents of stolen passwords shot up 689 percent against the monthly average over January. At least five of the 19 exchanges suffered attacks that resulted in the loss of $80 million in cryptocurrency.
50 active botnets are also continuously attacking both users and exchanges, the report claims. Over half of the malicious traffic is coming from the US, while the Netherlands supplies 21.5 percent.
The botnets are being fed new members by Trojan horses, a type of malware that often disguises itself as being a harmless file or program. When it is interacted with, a virus forces the machine to become part of a network of enslaved computers – or botnet.
Usually, computers contribute their computing power to complete a task – like mine a cryptocurrency or crack a weak password. Recently, Brazil was dealing with their own Monero-mining botnet , stemming from a zero-day attack on MicroTik routers.
While the report concedes that phishing attacks are still prevalent, hacking tools are becoming more sophisticated and properly attuned to cryptocurrency theft. It notes that attack patterns are resembling patterns of hi-tech bank heists, using modified software to target exchanges – who are simply not prepared for the worst.
“Increased fraudulent activity and attention of hacker groups to the crypto-industry, additional functions of malicious software related to cryptocurrencies, as well as the significant amounts of already stolen funds signals that the industry is not ready to defend itself and protect its users,” said Ruslan Yusufov, the Director of Special Projects at Group-IB.
These factors are only compounded by an apparent ignorance to security basics. Both users and exchanges are not making use of two-factor authentication (2FA). Even more startling – of the 720 compromised accounts, one in five used a password shorter than eight characters.
It’s worth mentioning that previous studies have concluded exactly the same thing: that cryptocurrency exchanges have terrible password security which leaves users vulnerable.
The report further suggests that investors pay close attention to what they post on social media. One should never leave “traces” on social media that suggest that they possess any cryptocurrency – and avoid carrying out any exchange transactions over public Wi-Fi.
Now, more than ever, its also a good idea to increase your knowledge of phishing attacks , and pay attention to who you blabber to about cryptocurrency in public. Set a really strong password and until the exchanges sort out their security, don’t keep too much on any particular one.
Do your research when choosing a wallet , and by the Bitcoin of Satoshi Nakamoto – enable 2FA on all the things!
Big brother is here, and his name is Facebook
In his book 1984 , George Orwell detailed a dystopian world wherein a person or persona called “Big Brother” saw everything that people did and where the central government pushed its agenda through propaganda, spying, monitoring, and thought controls.

That book was published in 1949. It is now 2017, and while we do not exactly have a Big Brother persona governing us, the Orwellian scenario is pretty much familiar. And it is not by means of some ultra-fascist government or political party. Rather, our loss of privacy and Big Brother’s influence on us are brought about by none other than our penchant for sharing on social media.
What privacy?
In 2013 Vint Cerf, who is considered as the father of the internet, said that “ privacy may actually be an anomaly .” Throughout history, people preferred communal settings in just about anything — the concept of solitude and privacy was something limited to monasticism.
Greg Ferenstein outlined the history of 3,000 years of privacy through 46 images. You might notice that history agrees with Cerf — and the artworks and imagery at least showed how people did things on a communal nature. It was only during the industrial revolution that we started to have a preference for privacy.
And with the rise of social media, that cycle means we are now moving again toward loss of privacy.
Imagine how much people have been sharing online, with friends and even the public. This includes photos, status updates, locations, all that while tagging friends who may not be aware they are being connected with photos, events, and places.
It’s not even limited to Facebook. No matter how little you share, all the meta data involved in just about anything you do online can constitute your digital persona.
All of these digital crumbs , so to speak, paint a digital picture of us, which bots, machines, and even data scientists, can lead to our digital makeup. Add to that the evolving technologies of facial recognition and machine learning — this means tech companies might know more about us than we do.
And this is extremely useful to anyone who needs to do any customer targeting. Ask advertising agencies and marketers.
In fact, ask Facebook.
Did you know that the social network may have the capability to listen in even when we are not actively sharing information or using the mobile app?
Facebook may be listening
You heard that right.
Given the amount of permissions we give social networks when we install apps on our mobile devices, we might as well just hand them over privileged access to our personal lives. With passive listening technologies, for instance, Facebook might be able to eavesdrop on conversations.
In 2016, a University of South Florida mass communications professor, Kelli Burns, shared her observations that the Facebook app delivered content based on things she mentioned in a conversation.
The idea that Facebook is passively spying has since been debunked, and Burns herself said her comments may have been taken out of context. However, this does not preclude the fact that Facebook itself has admitted to using smartphones’ microphones whenever necessary. “We only access your microphone if you have given our app permission and if you are actively using a specific feature that requires audio,” it said in a statement.
This refers to app features like song recognition and video capture, among others. However, it does not discount the fact that Burns observed a few relevant ads to be pushed in her feed when she mentioned certain keywords.
It all boils down to the permissions you have granted Facebook when you install the app. In most cases, granting permission is an all-or-nothing affair. This means you cannot cherry-pick the permissions to grant or deny when installing an app. You either accept or decline.
What you can do
This does not mean we can just simply let Facebook or other applications get away with potentially being able to eavesdrop on our conversations in order to “serve better ads”.
The choices here involve four things:
Uninstall the social networking apps
Find alternative ways to run the applications or use alternative ones
Find apps that can block social networking apps from recording audio
Switch to secured and private decentralized social networks
My first solution is quite drastic, but for people who are really paranoid about their privacy, then it is a good choice. Facebook is known to be a resource hog anyway — it reportedly shortens battery life significantly, due to its need to refresh and update on a regular basis. Thus, uninstalling apps like Facebook can help both improve your privacy and reduce battery drain.
On the second solution, there are alternative applications to Facebook and Messenger. For example, you can easily access the social network through your mobile web browser and set it to “desktop mode”.
There are also alternative apps like Fast and Friendly that give you access to the social network without the added overhead and features that the official app has. You can also use Telegram which ensures encryption and privacy across all communications.
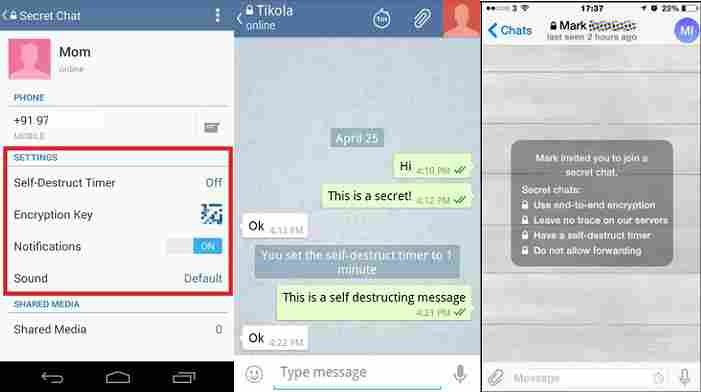

Thirdly, you can take control of your smartphone’s mic through another means. On Android, an app called RYL or “record your life” lets you do just that.
It compiles a live recording thus letting you keep track of your daily activities (at least the audio) for up to seven days. The added benefit? Because RYL locks the mic for its own use, other eavesdropping apps (Facebook, Google Assistant, etc.) will not be able to listen in.
There is a fourth alternative that is even more drastic – it might not exactly please avid Facebook users. You can leave Facebook in favor of other social networking services. But what exactly can we look forward to in social networking, when Facebook seems to be the apex of social networking apps today?
Perhaps a technology that offers more transparency, security, and assurance of user benefit would be a better alternative. Case in point: With the rise of blockchain technology as a distributed means of accomplishing transactions, exchanges, and digital contracts, this can certainly include social networking as a natural extension of information exchange that offers both privacy and transparency. This is what Nexus , a new secured and decentralized cross-platform social network is planning.
By running its platform on top of blockchain technology, Nexus integrates social networking, crowdfunding, and even e-commerce features embedded. Nexus is aiming to “eliminate all invasion of privacy that large corporation are currently performing” according to its founder, Jade Mulholland.
Toward the future of social networking
We are at an era wherein we have chosen to give up our privacy all for the convenience of being able to share and engage with our friends online. The more we share, the lower our privacy becomes. Social networking does not have to stop there, however. And we do not need to entrust all our social connectivity needs to a single company.
Perhaps decentralization is key to ensuring a secure social network built for the long run. Nexus is actually launching its initial coin offering (ICO) , which aims to raise resources and give users the chance to own a part of the social network through cryptographic tokens. Where blockchain-powered social networks will lead us , only time will tell. But it seems that the wave of the future is focused on decentralization, auditability, and flexibility offered by the blockchain.
Your privacy should still be considered sacred, especially if it pertains to what you say to another person face-to-face. If you are worried about your smartphone or other device listening in via its apps, you should act now, in order to further protect yourself against eavesdropping, which is very real.
Enjoyed this post? Read these next: – This creepy tool reveals how Facebook’s AI tracks and studies your activity – Facebook tracks scary-specific details about your life. Here’s how to find what it knows
We sometimes update and/or re-publish articles from our archives that are fun, informative, or highly-relevant… like this one.
Lightning Labs CEO is giving scholarships to female blockchain developers
Lightning Labs co-founder and CEO Elizabeth Stark has announced a scholarship for female blockchain developers.
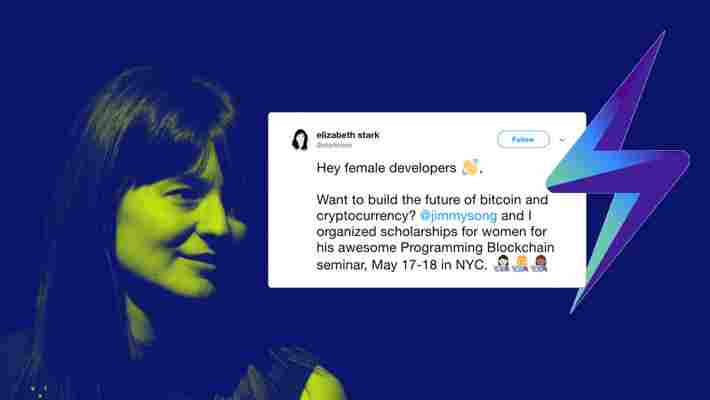
In a post on Twitter, Stark said that she and Bitcoin developer Jimmy Song have secured several scholarship packages for the upcoming Programming Blockchain seminar, which is scheduled to take place on May 17 and 18 in New York City.
The scholarships will cover the admission fees for the full two-day course, which usually costs $4,000. One thing to keep in mind is that scholarship recipients will be responsible for any travel expenses “ to and from the venue.”
Women developers can apply for the scholarship by filling out the form here . The form is rather simple other than a programming challenge that the aspirants are required to solve.
As Stark has already suggested , those interested in attending the seminar can learn more about the curriculum here .
There is a significant gender gap in the blockchain and cryptocurrency world (though the precise extent of the gap is still a point of contention ). Indeed, the Lightning Labs chief herself has previously suggested that the gender gap in blockchain might not be as severe as it’s made out to be.
Still, efforts such as these are appreciable to help narrow this gap and get more women into the field.

Leave a Comment