Nearly 400 Drupal sites infected with malware that secretly mines cryptocurrency
It seems like there’s no stopping the crypto-jacking epidemic, as hackers continue to steal unsuspecting users’ computing power to mine cryptocurrency.

Security researcher Troy Mursch from Bad Packets Report has discovered that a number of websites using an outdated version of the Drupal Content Management System are being victimized by hackers for crypto-jacking.
While the primary targets of this attack — which hit some 400 sites — are US-based government entities and educational institutes, multiple tech firms’ sites have also been infected with the virus.
A list of affected websites compiled by Mursch include those of the US National Labor Relations Board (NLRB) , Chinese tech company Lenovo, Taiwanese network hardware maker D-Link, and the University of California, Los Angeles (UCLA).
Government-run websites in the US, Mexico, Turkey, Peru, South Africa, and Italy have also been affected.
Mursch discovered that all of the infected JavaScript codes were pointing to the same domain name ( vuuwdom ) and same Coinhive key, implying that it was a single individual or entity behind all of these attacks.
Mursch’s previous research had found nearly 50,000 websites to be running crypto-jacking campaigns, many of them unwittingly.
An interesting fact about all of these attacks is the hackers’ mining service of choice — there’s a clear preference for Coinhive, which is responsible for more than 80 percent of all the infected websites.
Coinhive received some legitimacy after it rolled out a feature that required user consent before their computer could be used for mining. The Coinhive service along with this feature was even integrated by UNICEF to fund its charity for children in Bangladesh.
However, researchers have found that the ‘opt-in’ version is not usually very popular with websites, and they chose to integrate Coinhive with their website in a way that doesn’t inform the users.
It is high time that Coinhive halts its services that allow for mining without the knowledge of the user, and keeps only the mandatory opt-in version moving forward.
There’s no way for a user to know if their computer is being used to mine cryptocurrency through Coinhive unless they notice the high CPU usage on their device, and investigate the cause.
Thankfully, there’re ways to stop these cryptojacking malwares from exploiting your CPU’s computing power, and you can read all about them here .
Those interested in the detailed Bad Packets Report on this attack, can read it here .
Opera plans to add a cryptocurrency wallet to its desktop browser
Handling cryptocurrencies is about to get easier, as Opera becomes the first major desktop browser to include a cryptocurrency wallet, negating the need for third-party extensions or applications. In doing so, Opera has adopted an interesting approach to security.
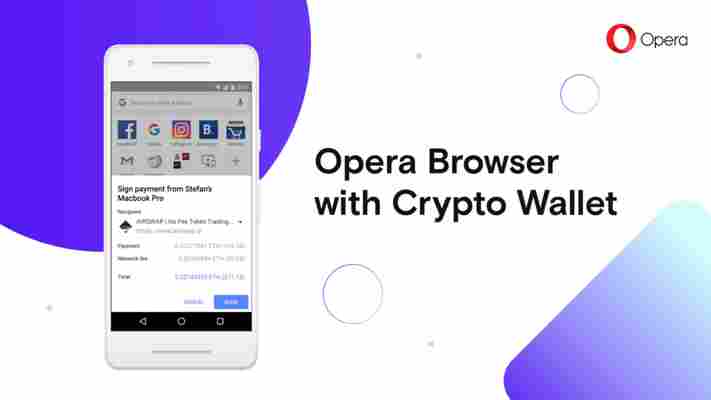
The desktop wallet (which supports Ethereum, its tokens, and collectibles) synchronizes with the cryptocurrency wallet integrated in the Android version of Opera since June of this year . When a user wishes to send a payment, they sign transactions using their phone’s built-in fingerprint reader, rather than typing out a long passphrase.
Passphrases can be forgotten. They can be stolen. The biometric approach, although not perfect, is, at least in theory, more secure and less liable to result in irretrievable coins.
Funds and assets — and the secure cryptographic keys associated with them — are stored locally on the user’s phone, rather than on a remote server somewhere. To connect the mobile wallet to the desktop browser, the user merely has to scan a QR code.
“After making crypto payments smooth and easy on mobile, we wanted the find the perfect solution for PCs”, said Opera EVP of Browsers, Krystian Kolondra, in a statment. “We realized the best way is to utilize our new mobile crypto wallet technology and to give our PC users access to it.”
Opera is making a big bet that blockchain and distributed apps (dubbed Web 3.0 by some) will become mainstream in a meaninful way. By adding this feature, it positions its browser at the heart of it.
“Our next aim is to make crypto-integration mainstream,” said Kolondra. “We believe blockchain technology has the power to transform the web of tomorrow and expet it to make a big difference in the years to come.”
Opera promises its browser cryptocurrency integration will roll out to users “soon.” Those wishing to get a sneak peek can register their interest here .
Scam Alert: ElectrumPro is not an upgrade to Electrum
If you are starting a new brand, remember to buy all the domains associated with that name. Electrum is learning this the hard way.

Electrum, a popular bitcoin wallet service, uses electrumrg as its primary web address. “An alleged scammer has since bought the similar-sounding om domain, which they’re using to mimic Electrum’s services. It’s styled as Electrum Pro, “the world’s most popular bitcoin wallet.”
Electrum took to Twitter to clarify that it does not own electrumom and that it is likely a ‘bitcoin stealing malware’.
On primary inspection, ElectrumPro leaves no doubt about it being a scam. The website attempts to present their product as an upgrade to Electrum as if it belonged to the same team.
Their website lists 4 team members with broken GitHub links and no other social media profiles. The names do not ring a bell in the blockchain community either. All community links are broken, except for a Twitter account with just one tweet:
It is basically a course in “How to spot a scam 101”.

Leave a Comment